What is IDSnet?
IDSnet is a network intrusion detection system
developed at the Informatics and Mathematical Modelling department of
the Technical University of Denmark (DTU), for use in detecting and
analysing misuse behaviour in large computer networks.
The current version of IDSnet is a pure
software implementation, which runs under the Linux operating system.
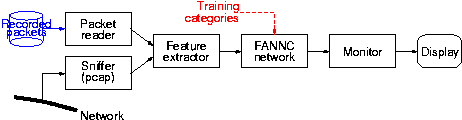
The system can be set up to use one or more sensors which observe
passing traffic in a network or subnet, or which analyse pre-recorded
packet traces. Each sensor is built up as shown in the figure:
A human operator of the system controls it from a GUI, from which it
is possible to select:
- the types of attack to be considered,
- the range of network addresses and ports to be considered,
- parameters used in training the IDS.
When multiple sensors are used, their results can be correlated at a
central site.
Neural Network Classifier
IDSnet is based on a neural network classifier
which efficiently and rapidly classifies observed network packets with
respect to attack patterns which it has been trained to recognise. As
in most IDSs, classification is based on a set of descriptive
features which characterise the packet. The
values of these features are determined by the
feature extractor, which passes them on to the
actual classifier.
The neural network uses the FANNC algorithm introduced by Zhou, Chen
& Chen. Technically this is a multilayered feedforward network
which uses supervised training, and which:
- can be trained rapidly,
- can be trained incrementally,
- once trained, can perform fast and accurate classification of
its input.
This makes the FANNC network well-suited for use in an IDS, where it
may be necessary to modify the classifier at short notice to take new
patterns of attack into account.
Suspicion
IDSnet uses the neural network to classify
individual network packets observed in the network according to the
attack pattern or patterns to which they most probably belong. For
many types of attack, observation of a single suspicious packet is
insufficient to identify the attack with certainty, and it is
necessary to observe the behaviour of the network over a period of
time. Typical examples are (D)DoS or port scanning attacks, where it
is in practice impossible to conclude that an attack is taking place
before a considerable number of suspicious packets have been observed.
IDSnet introduces the concept of
suspicion for
each network connection to deal with this. If several packets
characteristic of the same type of attack are observed for a given
network connection, the level of suspicion
rises; when normal packets start to appear again, the level of
suspicion falls. If the level of
suspicion rises above an alarm threshold
defined by the operator, an alarm is set off.
Operator's View
Every suspicious packet originates from a suspect and has a particular
victim as its target. Via the GUI, the operator can see graphs showing
the development in the levels of suspicion associated with the suspect
and victim for the connection with the highest level of suspicion at
each instant of time, in an observation window which terminates at the
current instant.
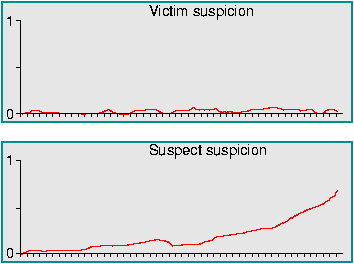
By clicking on one of the graphs, the operator can obtain information
about which IP addresses are associated with the suspect or victim for
the connection with the highest level of suspicion at a given
instant.
The operator can, if required, filter the results so as to
exclude unwanted data, for example from suspicious connections which
have already been analysed, and can direct the system to perform
detailed logging of network traffic associated with particular attack
periods, suspects and victims.
Distributing the IDS
IDSnet is designed for use in very large
distributed systems, such as those which make use of the Grid
paradigm. In systems of this type, a common requirement is for the
IDS to be distributed, with sensors in individual sub-nets.
IDSnet is designed to be configured in a
hierarchical manner, where sensors at the lowest levels in the
hierarchy communicate the results of their analysis up to the root
node:
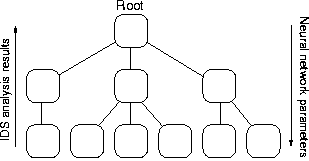
At the root node, the results from the various sensors can be
correlated to give a better picture of the development and possible
source of the attack.
In the reverse direction, the root node has the responsibility of
disseminating new sets of parameters describing the neural networks to
be used within the sensors. This enables the operators to ensure
that all sensors are kept up to date with the latest information
obtained from the learning processes.
For further information
You can find contact information here.



